Cyber security of border controls at Amsterdam Schiphol Airport is not adequate
An audit by the Netherlands Court of Audit has revealed that the cyber security of the border controls operated by Dutch border guards at Amsterdam Schiphol Airport is neither adequate nor future-proof. Few, if any, security tests are performed on IT systems; the software currently used for two of the IT systems has not passed the requisite approval procedures; and the systems are not linked up to the detection capacity of either the Dutch Ministry of Defence or Schiphol N.V.
Hardly any action has been taken to protect IT system used for border controls
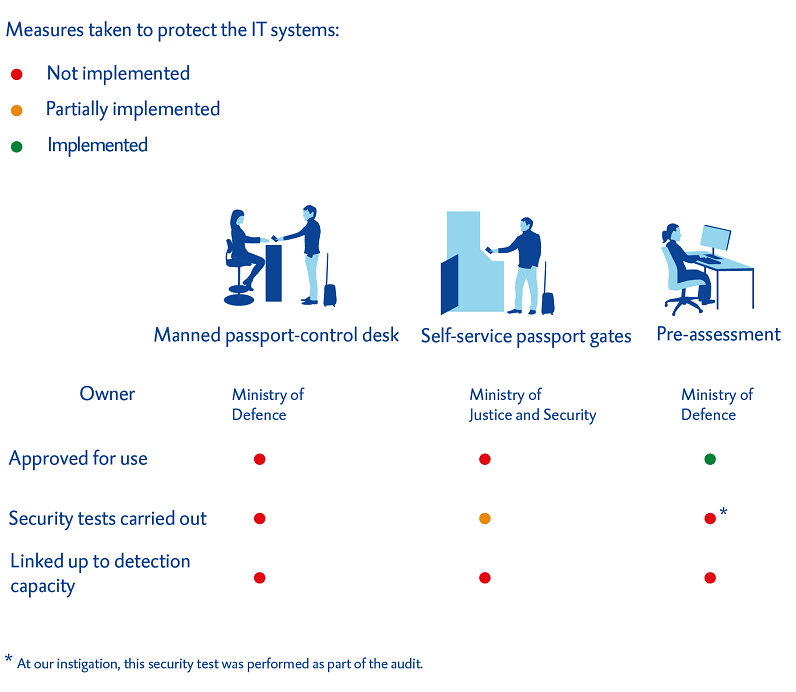
Handling almost 80 million passengers every year, Amsterdam Schiphol Airport is not merely the Netherlands’ main airport, it is also a vital gateway to Europe and the European Union. Passengers entering or leaving the Netherlands via Amsterdam Schiphol Airport are checked by Dutch border guards either at manned passport-control desks or at self-service passport gates. Passengers from outside the Schengen Area are also screened before they arrive at the airport, during a procedure known as a pre-assessment. All three forms of border control come with their own IT systems.
The cyber security of these systems is crucial in preventing digital sabotage, espionage and cyber crime. If the IT systems underlying border controls are disabled by a digital attack, the border guards will not be able to operate more than very limited border checks. The potential consequences are long passenger queues and delayed or cancelled flights. Another risk is that of foreign intelligence services using cyber espionage to manipulate data, so as to make it easier for people on the run from the police to cross the border.
Two of the IT systems used for border controls have not been approved
The Ministry of Defence’s security policy describes the security procedures with which all IT systems used for border controls are required to comply. IT systems may be taken into use only once these procedures are in place. However, two of the three IT systems have not been tested to confirm that they are adequately protected against cyber attacks. The systems used for the manned passport-control desks and the self-service passport gates have not fully completed the Ministry of Defence’s approval procedure.
Insufficient security testing of IT systems used for border controls
Although the Ministry of Defence’s security policy also stipulates that annual security tests should be performed, we found that in practice the three IT systems are subjected to very few – if any – such tests. Indeed, the systems used for the pre-assessments and the manned passport-control desks have never actually been tested. Although a security test was performed on the self-service system, this was more limited in scope than originally intended, and not all the resultant recommendations were implemented. This means that there is a risk of unidentified vulnerabilities in the system remaining undetected and of their being open to misuse by the perpetrators of cyber attacks.
Insider threat: a realistic risk
For the purpose of this audit, and in the knowledge that the Ministry of Defence had not done this to date, we asked for a security test to be performed on the IT system used for pre-assessments. The starting point for the test was an insider threat, i.e. a cyber attack perpetrated by an official from the Ministry of Defence who has access to the Ministry’s network but is not authorised to access the pre-assessment system. This is a realistic risk, given that 60,000 Ministry officials have access to its network.
The test identified 11 vulnerabilities, including the use of a standard password that could be traced with the aid of the (Googled) user manual. The test also revealed, for example, that emails could be sent on behalf of Ministry officials, such as the Chief of the Defence Staff. The use of a seemingly reputable sender can induce the recipient to click on a fraudulent hyperlink or to unwittingly install malware.
The test also revealed that, by combining a number of vulnerabilities during a sophisticated cyber attack, an attacker would be able to manipulate the pre-assessment system so that the system would report that a passenger was not on a list of wanted persons, even though he or she was. The Ministry of Defence has now removed the vulnerabilities so as to rule the possibility of such an attack.
IT systems used for border controls are not connected to Security Operations Centres
Although the Ministry of Defence’s security policy also stipulates that annual security tests should be performed, we found that in practice the three IT systems are subjected to very few – if any – such tests. Indeed, the systems used for the pre-assessments and the manned passport-control desks have never actually been tested. Although a security test was performed on the self-service system, this was more limited in scope than originally intended, and not all the resultant recommendations were implemented. This means that there is a risk of unidentified vulnerabilities in the system remaining undetected and of their being open to misuse by the perpetrators of cyber attacks.
Recommendations
Border controls are set to undergo further automation in the coming years. Their complexity and dependency on IT is also set to grow. With these future developments in mind, it is important to guarantee an adequate level of cyber security at this point in time. Given that the Ministry of Defence already possesses the necessary expertise, our recommendations centre mainly on ensuring that everything possible is indeed done. We find it incomprehensible that this has not been the case to date.
This audit was launched in the middle of 2019. It describes the situation before the coronavirus had reached the Netherlands. We presented our audit findings to the responsible ministers precisely at the time when the measures to combat the spread of the coronavirus came into effect and the Dutch government was compelled to direct all its energy at managing the crisis. Our findings and conclusions relate to events that occurred in 2019, and have not been altered by the grave developments that have followed in 2020. Despite the difficult circumstances, the ministers concerned were able to respond to our conclusions and recommendations, thus illustrating how the Dutch democratic system, including the independent audits performed by the Court of Audit, continues to operate – even in the exceptional circumstances prevailing in the spring of 2020.